Internet Connection Sharing
Internet Connection SharingInternet Connection Sharing
Even if your all gung ho about getting to the Internet to meet some new, friendly people, talk about their culture, and then wipe them off the face of the earth in StarBlasters 3D Mega-Expansion Pack IV - Online!!!, you still need to do first things first. And the first thing is to have your Local Area Network (LAN) working. If you haven't done that yet, make like a Monopoly player and go straight back to section The Local Area Network, don't pass "Go," and don't waste your $200. If you don't have your LAN functioning among the computers inside your own house and between the computers and the router, then your chances of getting them all sharing an Internet connection are grim.
OK. Now, you've got your LAN a hummin' and all your computers are chatting like Aunt Patty at your last family reunion after she'd had four glasses of wine. Your kids just used the computer upstairs to print 100 pages of "Hi Daddy!" or "Hi Mommy!" or "Hi Parental Unit!" in great big letters in just the last 10 minutes to the printer in your office. Even the cat just sent a fax to PetsRUs for more catnip. That's great! Now, it's time to move on to the next challenge - getting your Internet connection shared to all the devices on your LAN, while keeping everything as safe as possible. With any luck, this will turn out to be pretty anti-climactic because you've already done a good portion of the work.
Permissions and Rights - Are You Allowed to Connect More Than One Computer?

Now, hold on there, hombre! You did read your Acceptable Use Policy as mentioned in the section Want to Host an Internet Game Server? Check First, right? Yeah, I know you skipped that section. It's OK. However, you really should check your ISP's policy on connecting multiple devices if you haven't already. Most ISPs don't care and many even will sell or rent you the equipment (they recommend) to help. A (wireless) router/firewall may even have been included with your ISP's "connection kit" (or whatever they call the hardware and software supplied with your new service). Other ISPs say it's OK to hook up multiple devices if you pay them extra. Some just say, "No. One computer and one computer only." (Luckily, this position seems to be rapidly disappearing.)
Don't hope that you can clandestinely hook up your desktop PC, your laptop and your Xbox 360 and the ISP will never know. Even if you are going through a router, which masks the devices on the other side, your ISP can tell if they choose to check. That said, most ISPs nowadays understand that a house with multiple computers, gaming consoles and other networked devices is just the way things are. They've learned to embrace it. (As in, they've learned they can make money on it by selling you upgraded packages with faster connections and equipment to support multiple computers and other devices like the Xbox 360, iPad and TiVo DVR.) Assuming this is not a stumbling block, let's move on.
Internet 101
In order to understand some of the things that will be done while setting up your broadband sharing network, it's important to have a basic understanding of how the Internet functions. There are a number of really good web sites with tons of information on the subjects introduced in the next few sections. This is intended to be really brief introduction with just enough information to help make sense of the tasks to be done here.
Introduction to the Domain Name Service
We need to digress a moment and talk briefly about how domain names and IP addresses work on the Internet. First, understand that the Internet operates on IP addresses like 121.22.47.219 rather than (domain) names like www.neatwebsite.com. People, however, have a terrible time remembering numbers, so a way was devised to equate a name to an IP address. When you open a web browser and go to the URL http://www.neatwebsite.com/, something interesting happens. Remember those Domain Name Servers (DNSs) that your router gets from your ISP (or that were explicitly given to you by your ISP)? The purpose of a DNS is to translate names like www.neatwebsite.com into an IP address your browser can use.
It's a lot like the process of looking up someone's name in the phone book; you translate a business' or person's name into a telephone number in order to connect to them by telephone. In DNS parlance, this is called "resolving" the name.
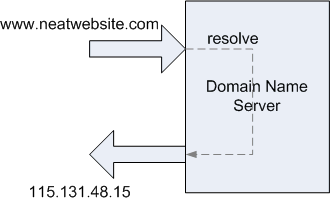
Your browser will consult one of your ISP's DNS servers and ask for the IP address that has been assigned to www.neatwebsite.com. The DNS server will respond with the IP address. Your browser will then make a request for a web page from the web server at that IP address. Every name you type into your browser's address bar must eventually resolve to a single, unique IP address. When the web server sends you back a web page, it sends it to the IP address that was included in the request. Just like the web server at www.neatwebsite.com, your (return) IP address must also be unique. Otherwise, there would be no clear path for the web page to find its way back to you.
Private IP Addresses
So now you might be asking yourself why talking about DNS servers was important when the topic is supposed to be your router. (Go ahead. Ask yourself. We'll wait.) Recall that when we set up our internal network, we used IP addresses starting with 192.168. If you stop and think for a moment, thousands upon thousands of people may have purchased the same router that you did. Many of those people left the internal LAN network at its default settings (e.g., 192.168.0.1). That means that at any given moment there are probably thousands of devices connected to the Internet with their LAN IP address set to 192.168.0.1, 192.168.0.2, etc. Why don't web servers on the Internet get confused when trying to figure out which 192.168.0.2 to return a web page to? The answer is that servers on the public Internet never see or use those addresses.
IP addresses that start with 192.168 are special ones that are called "private" or "non-routable" IP addresses. What this means is that these addresses have been set aside for use by businesses and home users to use internally. You will never find a public web server at the URL http://192.168.0.1 for example. (You could, however, create your own internal "Intranet" web server at that address, and that's fine.) Likewise, the return IP address for the web page you requested would never be 192.168.0.2, for example. It will always be the IP address that your ISP assigned (temporarily or statically) to your router. All Internet data destined for all computers and other devices on your LAN, initially arrive at your router using that public, routable IP address. It's up to the router to figure out which computer or other device attached to your LAN should receive the data (if any).
Introduction to Network Address Translation
How does a request for a web page from one of the machines on your internal LAN to a web server somewhere out on the Internet ever get back to right machine? After all, we purposely assigned one of those private IP addresses to it (either dynamically using DHCP or statically), and those can't be used on the Internet. The answer is that the web server that is out on the Internet never sees that private IP address. Instead, it sees the unique, public, "external" IP address that was given to you by your ISP (again either dynamically or statically). That IP address is guaranteed unique. How this gets done is part of the magic that is your router. The majority of home network routers are "NAT-enabled" routers. That means the router comes out of the box ready to perform what is known as Network Address Translation or "NAT". For this discussion, the simple explanation is that the router will note a request made by a device on the inside LAN that is destined to a device on the Internet (or WAN). This would be something like your web browser requesting a page from 115.138.48.15 to use our http://www.neatwebsite.com/ example above. (Remember, your browser would have already contacted a DNS server to resolve the name www.neatwebsite.com to its unique, public IP address.)
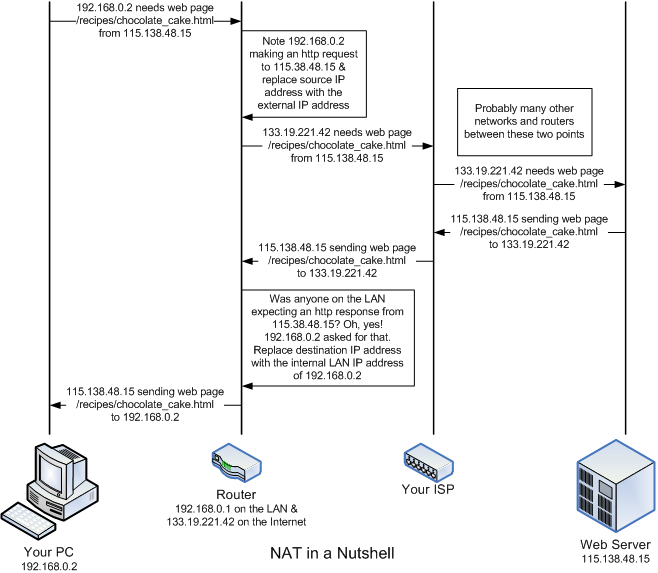
The router will replace the internal, private IP address (e.g., 192.168.0.2) originally found in the request as the source address with the public IP address assigned to your router and send the request on to the web server on the WAN connection. (Let's say it's 133.19.221.42 for this example.) When the web server returns the page you requested, it will send it addressed to the requestor's source IP address (which the router changed to your public IP address). (The source IP address for the request becomes the destination [or target] IP address for the response.) When the web page arrives back at your router, the router will determine which machine on the LAN made the original request for the page. The router then replaces the unique, public IP address given as the destination for the page with the internal, private IP address of the machine that the original request came from. Then is transfers that data onto the LAN-side of the router for the originating device to receive. This is how the router shares your public (WAN) IP address among the devices on your LAN. As far as the world knows, you only have one device on the Internet. Your router knows better. I took about 30 shortcuts in that explanation, so research the topic on the Internet if you want to know more.
I will take a paragraph to note that there are routers that do not use NAT or use NAT only on certain portions of the internal LAN. These routers are most often used by medium to large businesses (and assorted computer geeks that just can't help themselves). This type of network is beyond the scope and goal of what this guide is trying to accomplish. If a router isn't using NAT for a portion of an internal network, then the devices on that portion of the network must be assigned unique, public IP addresses just like the router itself. Larger businesses (like Amazon.com and Google.com just to name a couple) may have dozens of public IP addresses on both internal and external segments of their network. (I don't know the actual network layout of either of those companies, so I'm just making an educated guess.) Most home and small business networks don't have this need. (At least, not yet.)
Using NAT also provides a level of protection for your internal LAN. The enterprise-class routers that make up the major backbone of the Internet will not route private IP addresses in any direction. (Your typical home network router will usually route private IP addresses either way.) Since the IP addresses you are using are private, a hacker from afar cannot pretend to be a machine on your internal LAN by assuming one of your internal addresses. Such traffic would likely be squelched before it could reach you. Additionally, because of NAT function of your router, any packets sent from your Internal LAN appear to be sent by your router. A hacker would have to attack using your external IP address as the target. That's relatively simple to do since hackers tend to attempt to hack a range of addresses they know an ISP allots to clients. They also have to guess you are using NAT. That's also a safe bet. Using your external IP address as the target, a hacker would have to monitor the outgoing traffic from your router and construct a packet with what your router is expecting as a response (to an active request from one of the attached network devices) at a particular moment in time. Since the router's expectations change with every request made from an internal device, a hacker would have to monitor the traffic, find a request worth attacking and then generate and send respond very quickly (before the actual recipient does). This would only work if the attacker is very "near" to your router from a network perspective. In general, this is just not worth the effort. It's far easier to go after targets without firewalls or NAT addressing. Even today, there are ISPs that barring any effort on your part will connect a computer to the Internet with little or no firewall protection. Don't be one of those. If your ISP doesn't supply a firewall router with their service, go buy one of your own.
Introduction to Firewalls and Ports
In addition to the NAT capability, the typical home router will include some sort of "firewall." A firewall is a program built into the router to specifically permit or specifically deny different types of network traffic from passing through. In addition to IP addresses, which we've already discussed, a request for data (an email body, a web page, etc.) is also destined to a particular "port" at that IP address. The port is a delineated by a number from 0 to 65535. Having multiple ports allows a single IP address to be requesting multiple types of services over the Internet (and sending data in response to requests) in parallel. It also allows the same server to service more than one type of request. The ports from 0 - 1023 are called "privileged ports" and are assigned to well-recognized services. For example, when you a request to view a web page to a web server, it will usually be sent as a request to port 80 of the web server's IP address. (If the web page is being sent as a secure page to a URL beginning with https://, the port number will usually be 443.) As mentioned in the previous section, in order to find out the IP address of that web server, you first resolve its name using a DNS server. The DNS requests from your computer would be sent to port 53 on the DNS server. Since most residential customers aren't expected to run any public servers like a mail or web server, the firewall in most home routers will summarily deny any traffic from the Internet with a destination IP for your home that is attempting to use a port in the privileged port range. Ports above 1023 aren't officially assigned to a service, but many have become de facto standards. These are known as "unprivileged ports." Port 5109, for example, is an unprivileged port often used by AOL's Instant Messenger.
Most people think of a firewall only as a means for keeping unwanted or malicious traffic from the Internet out of your home LAN. While that is true, it is equally important that your firewall is keeping unwanted (or malicious) traffic from your LAN off the Internet. For example, Windows PCs periodically query for and advertise network services on ports 137, 138 and possibly 445. (See the trace log below.) If you are connected directly to the Internet without a router or firewall (software), you are probably emitting these requests at a fairly regular interval over the Internet. For the most part, nobody cares and you are just adding to the unwanted/unnecessary traffic on the Internet. Worse, for those that do care - the hackers - you're pretty well lighting a beacon exclaiming "I'm a noob, and I want someone to rape and pillage my machine, please!" Operating a PC on the Internet without a good firewall in place as the equivalent of smearing your naked body with honey and running headlong into a bear den while screaming at the top of your lungs. A NAT router with a firewall will (usually) keep this information from finding its way on to the Internet.
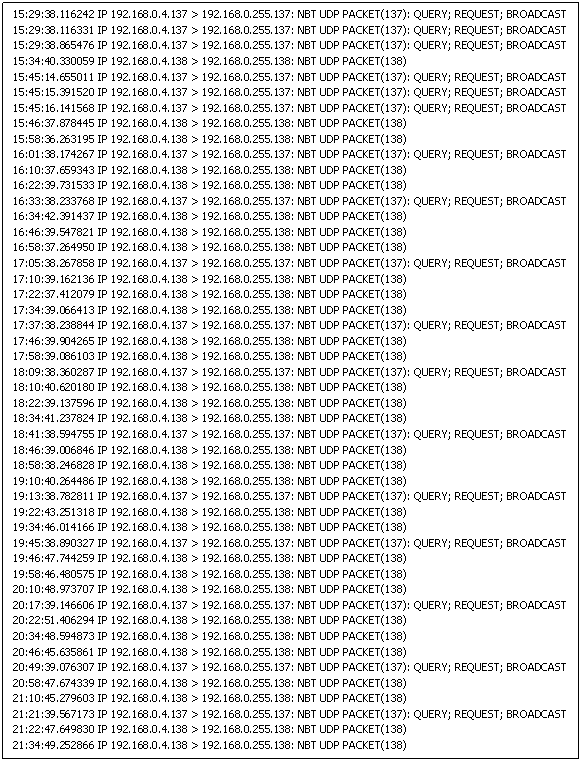
Network Trace of Microsoft Windows Machine Sending Out Periodic Broadcasts
Most ISPs now do a fair bit of screening traffic for you. For example, I log all network traffic that my firewall rejects. I'm paranoid that way. With my previous ISP, I had to stop logging the requests to ports 135-140 and 445 that my router denied. There was just so much of it, it filled my log up. My current ISP must be squelching that traffic somewhere upstream, because I see very little nowadays. A good router with a firewall will keep that traffic inside your LAN thus reducing the amount of useless traffic on the Internet. It also helps to make your home network and router less conspicuous and therefore, less of a target.

Firewall's also protect you to some degree from the effects of a Trojan horse program should you get one. The majority of the Trojan horse programs that I encounter in the wild are being delivered via email rather than an attack on my IP address directly. (The direct approach does not work if you have a reasonable firewall in service, so hackers have switched delivery mechanisms.) If a Trojan should slip through your virus/Trojan detection software (You do have virus/Trojan software on your machine, right?) and install itself, a firewall may still render it inert. If the Trojan's purpose is to wipe out your machine, the firewall won't stop it. However, a lot of Trojan's are designed to find a PC with high-speed connectivity and turn it into some sort of slave server. The Trojan will attempt to contact some sort of controller to let it know it's ready to receive commands. A couple popular use for this type of Trojan is to turn your PC into a host for illegal file sharing or as a sender for email spam. A well-configured firewall may possibly keep that the Trojan from contacting the controller and may keep the Trojan's controller from sending commands to the Trojan running on your local PC.
Most firewalls in home routers are "stateful packet inspection" (SPI) firewalls. With an SPI firewall, the firewall keeps track of all requests made by devices inside your LAN to destinations on the Internet (i.e., connections made to Internet servers). When traffic (a.k.a. a packet) from the Internet reaches your firewall, it should match one of the outstanding requests. If it does match, the firewall passes it to the LAN so it can reach the device that requested it. If it does not match, the firewall drops or rejects the packet. This essentially comes for "free" for router makers if they support NAT (and I can't think of one that does not). Since the router is already tracking connections for the purposes of NAT, SPI is already there.
There is a difference between dropping and rejecting a packet. If a packet is rejected, the router replies to the sender indicating the reason for the rejection. If a packet is dropped, the packet is simply squelched by the router with no indication to the sender what happened. Most home routers drop packets rather than reject them as this is simpler to implement and dropping packets is also stealthier. If your router tells a hacker it's rejected the packets they sent, they know you are there, but that they need to try another approach. If your router simply drops the packet, you don't appear to be there at all and presumably the hacker will go look for a likelier target.
This approach works for home users because most of us operate on an information "pull" model. That is, nothing is sent to a machine on our LAN out of the blue. We use a browser to request a web page and a web server somewhere on the Internet responds. When we get our email from an Internet email server, we make the request for it. Even when we play a game on the Internet, we usually join a centralized server; we proactively start the connection.

The providers of those services - the email servers, game servers, web servers, and so on operate on the model that requests for their services will be initiated from many locations outside of their "LAN." That is, they operate on a "push" model - they will be pressed into service as needed. Therefore, they require a different sort of firewall. That isn't to say your firewall is necessarily incapable of allowing you to host services. The section on Port Forwarding and Adding Firewall Rules goes into this in some detail.
Antivirus and Firewall Programs
Antivirus and Firewall ProgramsVirus Protection and Personal Firewalls

This section is intended more as a warning than as instruction. Once you have an Internet Connection Sharing network, especially one that's always on like Cable and DSL, assume that there are people (more realistically, automated programs) attempting to break into your LAN from the minute you first connect. There will be. The firewall in your router is there to stop the hacking and break in attempts. That will help stop viruses from being spread into your LAN directly from machines on the Internet. Unfortunately, it doesn't stop you from reading email or browsing to web sites with malicious code. Email is a popular source for Trojan horses and viruses. They are generally disguised at attachments to emails the senders hope you will think is legitimate. I used to get 1-2 virus or Trojan infected emails on an average week, but this has dropped dramatically. I believe this is because I have greatly increased the amount of spam filtering on my email server. I also suspect my ISP is proactively scanning email looking for Trojans and viruses. Another source of viruses and Trojans is web site that have infected code. In many cases, just browsing to those sites is enough to run the malicious code. A firewall does nothing to stop those. This is why having an anti-virus program such as Norton Antivirus or BitDefender to name a couple, is so important. If cost is an issue, Bitdefender's free version or AVG's free antivirus software are very good free alternatives. Equally important is keeping your antivirus program up to date. New or modified viruses and Trojans appear on a daily basis. Your virus definitions and engine need to be updated at that same pace.

Not all viruses and trojan horses get into a LAN via the Internet. Other sources include a (laptop) computer, CD-ROM, or flash drive that was introduced from outside your LAN. That said, attacks from the Internet will greatly outnumber those that come from outside. So, how bad is it? I log the traffic that my firewall rejects and drops (with the exception of the Microsoft file sharing query traffic that I noted above). I often see 50 - 100 port scans a day that are usually probing specific ports or certain port ranges. When I see a specific port that gets probed a lot, I generally research it on the Internet to find out that the Virus du Jour is.
Remember, not all attempts to break into the computers on your home network are made for purely malicious purposes (e.g., erase your hard disk or crash your system). The goal of many hacking attempts is to take over control of your computers to use them for a purpose (e.g., make them a "zombie" file server for serving illegal files or to make them email spamming drones), to search hard drives for personal data such credit card and bank account numbers or to log keystrokes from certain web pages and programs in order to obtain passwords. Therefore, it won't always be easy to detect that a machine has been compromised.
Even though your router has a firewall, it's still not a bad idea to have a personal firewall running on every machine on your home network. Microsoft started including one with Windows XP (and even turned it on starting with Service Pack 2), but there are others like Zone Alarm Free, which is free, and Zone Alarm Pro, which is the more-advanced commercial version, that are well worth looking into. This may sound a bit paranoid, but in fact it's really a good defensive move. If one of the machines on your LAN does become infected, the personal firewall on the other machines may stop it from spreading. It's not uncommon for the cool new "warez crack" of StarBlasters 3D Mega-Expansion Pack IV - Online!!! that little your Johnny got from his friend Billy (since we know your little Johnny would never download illegal software) to contain a little something extra. That "extra" being a virus. Once Johnny installs that software his machine is infected and looking for others to infect. A personal firewall on his machine may prevent the virus from successfully contacting other machines. More likely, firewalls on the other computers will keep the virus from spreading out of Johnny's machine.
Additional or Upgraded Hardware
Additional or Upgraded HardwareAdditional Hardware
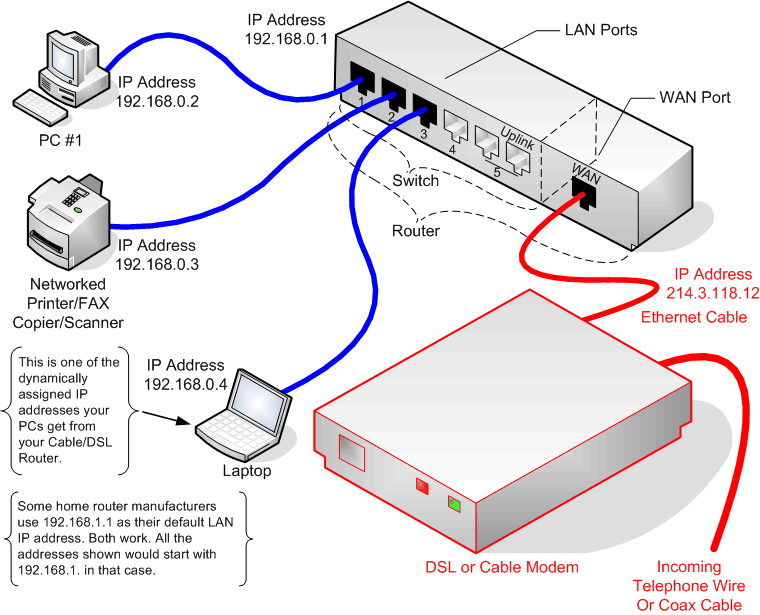
When I originally wrote this guide, I wrote it for two distinct groups of people: those that only wanted a Local Area Network (LAN) - generally for use in a small office - and those that were just getting a broadband connection in their home that they wanted to share. My approach then (and now) was that most of a Internet Connection Sharing network is exactly the same as a LAN plus a couple new components. The new components are those directly involved with connecting your home to your ISP - namely the cable or DSL modem and the network router (if you don't already have one and even if you, the ISP insists on using theirs). Some ISPs are also using a single device this serves both as the cable or DSL modem and as the combination firewall & router. (Unfortunately, a number of those only offer a single LAN port, so you would need an Ethernet switch to connect more than one computer to the network.) A wireless access point (WAP) may or may not also be present. We will also ignore whether the incoming high-speed connection is a coaxial cable (used for high-speed cable), a telephone wire (used for DSL) or something else in most of the discussions here. We've already discussed routers to some degree in the discussion of the LAN, but in this section, we address the equipment and configuration needed above what is needed for just the LAN.
Everything needed for the Local Area Network plus:

In the LAN examples, a simple Ethernet switch can be used to connect all the devices on your network together (or rather, connect the Ethernet cables from those devices). However, in the Internet Connection Sharing type of network, the router is often also the switch. Therefore, when planning your network, you run your cables to wherever your cable/DSL modem and router is. (Conversely, you can place the router wherever it's convenient to run the cables to. Just make sure there is a power outlet nearby.) The cable/DSL router is usually placed near the cable/DSL modem. However, you don't have to locate your cable/DSL router next to your cable/DSL modem if that isn't a good place to concentrate the cables to. (This point is moot is you only have a single device that functions as the modem and router.) Example 2 in the section on Planning Your Physical Network Layout goes into this possibility. You can also still use a switch in addition to the router if you prefer or if you need more Ethernet ports for your internal network than are supplied by the router. Example 3 (second floor) shows an example of this setup.
The picture below should look similar to the picture titled "Typical Local Area Network Setup Using Only a Switch" found in the section The Network Hub/Switch. As has been said before, a LAN is a subset of the BCS network. The additional connections and equipment are illustrated by the red lines in the picture below. The notional router being used here is similar to a switch, but with an additional WAN (wide area network or Internet) port. The WAN port is connected with an Ethernet cable to the DSL or Cable modem that connects to your Internet service provider's high-speed connection (e.g., coax cable or telephone line). In the next several sections, we discuss the modem and routers and what additional capability they bring to the table.
DSL/Cable Modem with Network Port
If you have cable or DSL Internet service, your high-speed modem connection enters your house as a signal either on a coaxial cable (cable Internet service) or a pair of regular telephone wires (DSL Internet service). Some device is needed to convert the incoming line to standard Ethernet protocol signaling on a standard Ethernet port. That is the job of the DSL or cable modem. Often, the DSL or Cable modem you use is supplied by your Internet Service Provider (ISP), so you may not have any choice about what you get. If that modem dies, you may have some flexibility in what you can buy as a replacement, however. I know that my local cable provider gives you the choice of buying or renting the modem from them or buying the modem yourself (from a list of recommended modems). DSL providers usually sell a specific modem to be used with their service.
Sometimes though, not having a choice isn't all bad. Often, DSL providers run promotions to give away or rebate the cost of the modem. I personally believe they make little or no money on sales of the modem itself. I researched my DSL modem on the Internet and consistently found it priced more than what my DSL provider sold it too me for. On top of that, my provider gave me a rebate toward the full purchase price. I believe that ISPs want the equipment they send out to be as uniform (i.e., as few different types) as possible. That makes it easier for the ISP's technical and customer service representatives to do their jobs.
Installation of your modem will either be done by your ISP or they will ship you a package with the modem and anything else you need to install the modem yourself. The latter option is termed a "self-install" package or kit. At one time, cable and DSL modems were almost always installed by the ISP, but both DSL and cable companies have started using self-install kits more predominately. I take that as a good sign as it means the ISPs feel that the technology has reached a point where untrained professionals (i.e., you) can be expected to install the modem with a good chance of success.
Install ADSL Low-Pass Filters (DSL only)

Asymmetric DSL (ADSL) is the most common type of DSL sold by telephone and DSL companies. With Asymmetric DSL, the download speed is faster than the upload speed; hence it's not symmetric or, rather, it is asymmetric. With ADSL, you may be supplied with and asked to install filters between your telephone jacks and telephone devices in order to begin using your DSL service. The one shown in the picture here is one of the ones supplied by my old DSL provider. There are also versions that take the place of a standard telephone wall jack. The reason these are needed is that your DSL service and voice telephone service share the same pair of wires. (If your DSL provider provisions a separate pair of telephone wires for your DSL, you will not need these filters.)
A simple of explanation for what the filters do is that voice quality telephone service requires only about 4 KHz of bandwidth. That's only a small fraction of the bandwidth a copper telephone wire is capable of carrying. Therefore, it's possible to have both telephone and DSL service sharing the same pair of copper wires. The DSL modem is smart enough to ignore the signal below the bandwidth reserved for telephone conversation (plus a buffer of an extra few KHz to separate the two and prevent crosstalk). However, your old telephone equipment is not that smart, so the filters block everything but the very lowest frequencies - the frequencies reserved for voice phone conversations. (Hence they pass the low frequencies and are called "low-pass filters.") My first DSL service used a separate phone line from my telephone, so I was a bit leery of using these at first, but after using them, I can say they didn't seem to adversely affect the quality of either the voice or DSL service.
There is a maximum of the number of filters you can install per household. For example, the limit on the ones I have is five total. That may sound like a lot, but don't forget you will need these for every phone in your house as well as devices like your Tivo (DVR) or other satellite TV DVR, fax machine, caller ID unit, answering machine, & computer modem (assuming you still need to dial in occasionally). You can daisy chained several phone devices off of one filter with no problem. That is, if you have a fax machine with both line in and phone out jacks, plus a caller ID with both line in and phone out jacks and finally a phone, they can be hooked together and into a single DSL filter without a problem. Take care to get and install two-line models of these filters if you have two incoming lines in your home (e.g., you have a separate line for your home and home office or separate lines for your telephone and your fax machine).
Connect the DSL or Cable Modem
Other than the physical input being telephone wire or coaxial cable, the cable and DSL modems can be treated more or less the same. (With FiOS, the ONT provides a standard Ethernet connection.) So the first step (if your ISP does not do this for you or if you are "self-installing" your modem) is to connect the coax or cable to your modem. For a DSL modem, the phone line clicks into the phone jack on the back of the DSL modem. (Don't confuse the telephone jack with the Ethernet port. For former is smaller than the latter.) The coaxial cable screws onto the cable connection on the back of the cable modem. Once you have done this, the rest of the installation is the same for either type of modem. (It is also the same from the point forward for FiOS.)
Next, you need to connect the Ethernet port on the modem to the WAN or Internet port on the router. The connection between the router and the modem may be one of those cases where a crossover cable (see the section on Cables) is necessary. The install kit will likely include a (very short) Ethernet cable, but it will not be a crossover cable in most cases. Some routers use MDIX (or auto-switching) ports on the WAN/Internet port, so a crossover may not be necessary. My approach is to try the cable supplied (assuming it is long enough to reach with your installation) and see if you get a link light. If you get one, great; if not, it's crossover cable time.
Typical Cable and DSL Modems
The figures below show an example of both a cable and DSL modem. We don't show a lot of choices here because there are many of them and generally your cable or DSL ISP chooses what modem you will be using. The ones shown here are reasonably representative of what is found in the wild.
| The Motorola SURFboard SB5100 is representative of cable DSL modems. The lights on the front show (from top to bottom), power, (cable) receive, (cable) send, online, PC/activity, and standby. |
|
| The back of the Motorola SURFboard SB5100 has (from top to bottom) a 10/100 Mbps auto-sensing Ethernet port, a USB port, a terminal for the incoming coaxial cable, and at the very bottom a jack for the DC power supply input. Some cable (and DSL) modems will allow you to connect PCs (or a router and a PC) to both the Ethernet and USB ports simultaneously (respectively) assuming your ISP will allow you to have two IP addresses. Generally, you would only use one or the other and we encourage the use of the Ethernet port if at all possible. |  Copyright 2010 Motorola Corporation |
| The Westell WireSpeed 2100 is typical of DSL modems. From left to right, the lights indicate USB traffic, Ethernet traffic, (DSL line) ready, and power. |
|
| The back of the Westell WireSpeed 2100 has (from left to right) an incoming telephone wire jack, a USB port (rarely, if ever, used), the input jack for the DC power supply, a reset button and the Ethernet port. Like the cable modem, either the USB or Ethernet port, but not both is generally used. (And we again encourage the use of the Ethernet port.) |
|
Router / Firewall / Switch (/Wireless Access Point)
The cable or DSL modem's job is to convert the incoming media of a coaxial cable or telephone line into a standard 802.11 Ethernet port. (That's also one of the purposes of the Optical Network Terminal [ONT] in Verizon's FiOS offering.) Typically, that one port is also assigned the single (static or dynamic) IP address that your ISP allots to your home or small office. The router's job is to share that one connection among potentially many devices on your LAN. It determines what network traffic should be routed from a device on your internal LAN to a device on the Internet and vice versa. I've often heard the anology that the routing function is like a traffic cop directing traffic. Really more analogous to a security guard at a private residence. If the router receives a network packet from one of the devices on your LAN that has a destination IP address that's outside, it will pass that packet through to the WAN or Internet. On the WAN side, the router will examine the packets it sees and if the packet matches the WAN IP address it is set to, it will pass the packet to the LAN (with some "adjustments" we will get into below) if there is a device on the LAN expecting it. The primary task of a router is to act as a gatekeeper or gateway.
Generally, residential (home) customers of an ISP are allotted only a single public IP address. That IP address may be issued dynamically using a DHCP server that the ISP maintains or it may be assigned statically. That single address only supports one networked device. The question then is how do you share this single IP address with more than one networked device from your LAN? You need some way of making all the computers and networked devices in your home appear to the outside world as a single device. Another task of the router is to do just that. (At least, that's the method used by most home and small office networks.)
I've seen several forum posts asking some variation of the question, "I only have a single computer to connect to the Internet. Is there any benefit to having a router?" In my opinion, the short answer is "Yes." While there is no technical reason why a single PC can't be hooked directly to the Ethernet (or USB) port of a cable or DSL modem, generally not a good idea. If you purchase, install, lock down, and monitor your PC using a good software firewall, connecting a PC directly to the modem may be fine. The problem is many people don't understand what it means to "lock down" their PC and leave too many ports open. Even fewer monitor their firewalls as they should. Microsoft's own Internet Connection Firewall has improved in the since the Windows XP Service Pack 2 release. Still, it often doesn't have the configurability and capabilities of a hardware router firewall. Commercial firewall software packages are better, but their cost is comparable to buying a hardware firewall router.
Typical Routers
The table below lists some typical wired Ethernet routers. The Wireless Networking Equipment section already listed some typical wireless Ethernet routers. The routers listed below differ in only that they do not have built-in WAP capability. These are becoming rare nowadays as the prices of the wireless-capable routers have dropped to match those without and the popularity of wireless networking has increased. Mostly, I see these used in small businesses that don't want the risk of having an active wireless network. (It's also possible to buy a wireless router and just shut off the wireless capability.)
| The Linksys BEFSR41 shown here is a cable/DSL router/firewall with a built-in 4-port 10/100 switch in the back for the LAN side. Linksys also makes a couple models with built-in wireless access points (WRT54GS), a single LAN port, and an 8-port model. The router is really only needed if you are planning to share an Internet connection. |  Copyright 2010 Linksys Corporation |
| The Netgear DG834N Rangemax is a router like the BEFSR41 above, but also includes a built-in DSL modem and an 802.11n wireless access point. Devices such as these take the place of a separate cable or DSL modem (like those shown in the previous section) and router. |  Copyright 2010 Netgear Corporation |
Additional Configuration
Additional ConfigurationAdditional Configuration for Internet Connection Sharing
You may have noticed earlier when we were configuring your router for your LAN connections, that there was a whole slew of settings we completely ignored. A number of those have to do with your wide area network (WAN) or Internet connection to your ISP. We didn't need to set them while we were concerned only with setting up the LAN, but now is the time. As with the previous sections, this section will attempt to teach by example. If you've made it this far, you're almost there.
Configuring Your External Internet IP Address
Most Internet Service Providers offer similar options to those you had to choose from for assigning the IP addresses for your LAN: dynamic IP address assignment using DHCP or static (fixed) IP assignment. (See Using DHCP IP Address Assignment for Automatic Configuration and Fixed/Static IP (Manual IP) Assignment, respectively.) Think about it this way, you are acting as an ISP providing Internet service for the networked devices inside of your home much as your ISP is providing service to your home. Many of the same procedures you used to set up your LAN are similar to what your ISP does for its customers but on a larger scale. Most ISPs offer dynamic IP (DHCP) service as their basic package - charging at least slightly more for static IP address accounts if they offer static IP addresses at all. Often, static IP addresses are offered only as "business" packages. Unless you are planning on running some type of services such as a web server or permanent game host server (again making sure that your service agreement give you the right to do so), dynamic IP service is fine for most home networks.
Connecting to Your ISP Using Dynamic IP Addressing
We'll start by assuming your Internet service is dynamic and uses your ISP's DHCP server to get the external IP address for your router. One thing that you might find a bit mind bending is that at the same time that your router is the DHCP server for the devices attached your internal home network (LAN), it is also a DHCP client to your ISP's DHCP server in order to obtain an IP address it can use to connect to the Internet. It can do both, and it won't get confused. Are you? Dynamic service from an ISP is so common that most routers are set up to work with it from the start. You may find that you are already connecting to the Internet at this point. It's still a good idea to go through the steps here and look at what the normal settings are.
As before, the first step in configuring the router is to log on to it. Do this by browsing your router's LAN address. For this exercise, I've set the router's LAN IP address to 192.168.4.1. All the LAN devices, therefore, are on the 192.168.4.0 network. If your router is still set to the factory default, browse to that IP address instead. You will need to make sure that the IP address of the Ethernet adapter on the machine you are browsing from is also on the same network. (In our example, that means it has an IP address beginning with 192.168.4.) If your router has DHCP enabled on the LAN by default, which most do, you will be given a valid IP address by the DHCP server. If not, you will need to manually set the IP address of the Ethernet adapter. You can check if you have a valid IP using Test 4: Checking for Valid IP Address. Browsing to the router's configuration main page is shown below. Your router's page will likely look different.
Login to the router with the password you set earlier. That will bring up the first configuration page, which for our example router looks like the following. (Your router may have a different first page. You need to find the page that lets you set the WAN or Internet IP configuration.)
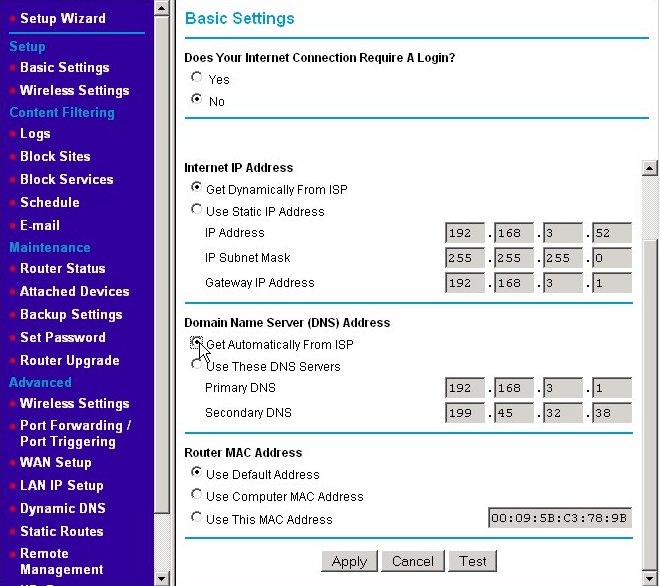
If they are not already selected, click on the radio buttons for getting your Internet IP address automatically from your ISP. This means your router should make a DHCP IP address request broadcast on the WAN to your ISP's DHCP server. You would also click the radio button to get the IP addresses of your ISP's DNS servers automatically. On most home routers, these are the default settings. If your router has these settings, you won't need to change anything. I'm changing from static to dynamic here so that you can see the changes. (It's quite possible that you will have full Internet connectivity the moment you hook up your cable/DSL modem to your router. The default settings apply to the majority of high-speed Internet users. Your router may not look like the one above but look for settings for configuring your WAN IP address and DNS settings somewhere on the basis, WAN, or Internet setup page.
In our example, we were using a fixed IP address of 192.168.3.52 for the Internet IP address. If you recall the discussion on routers and private IP addresses, any address beginning with 192.168 is not a valid public IP address. So how did I get such an address from my ISP? The answer is that I didn't. For this example, I've hooked a second router off of one of the Ethernet switch ports of my home's LAN. I'm treating my LAN as if it's my ISP's WAN. The "LAN" this router serves is a second, even more internal LAN. My reason for doing this is preserving harmony within my home. If I disconnect and reconfigure my real router to the Internet as I'm performing these examples and capturing screenshots, I tend to raise the ire of those people near and dear to me. Once you have had an Internet connection sharing home network for a while, try disconnecting it for an hour or two in the early evening. You'll make quick enemies. I guarantee it. That said, the actions you will take are the same. Just remember that IP addresses starting with 192.168.3 in my example represent the WAN or Internet connection and those starting with 192.168.4 represent the LAN. There are ISPs that use 192.168.x.x type addresses for the IP addresses they give their clients. This is somewhat rare though.
Press the Apply button to make the new settings effective. Occasionally when I do this, I can no longer browse the router's home page. If this happens to you, you may have lost your IP address. You may need to run the ipconfig /renew command to get a new one. (See the example in the section Changing the DHCP Server's IP Assignment Range.) The next screen shows the results of our actions.
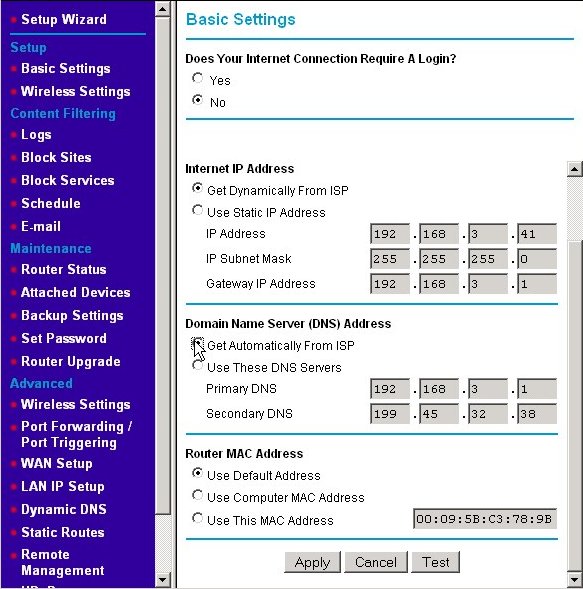
The IP address we received from the ISP's DHCP server is 192.168.3.41. The subnet mask, gateway IP address, and DNS IP addresses did not visibly change as these were already correct as my WAN settings. (Remember, I'm using a mock network inside my existing network. I just went from fixed to dynamic addressing in the example above. When you first connect your router to the Internet and apply your settings, the subnet mask, gateway IP address, and DNS values will likely change.) Most router manufacturer's put that addresses that were dynamically assigned in the text fields used for manual assignment, but grey them out (i.e., disable them from being edited.) Some just disable the fields and leave them blank, which makes it harder to see the effect of your actions.
Connecting to Your ISP Using Static IP Addressing
Connecting to your ISP using static IP addresses is much like setting up dynamic IP. You start by logging into your router as shown in the last section. However, you set the opposite radio buttons; namely, click on the Use Static IP Address radio button (also called "fixed" or "manual" IP addressing) and Use These DNS Servers radio button as shown below. (Again, the name on your router may be different. You're looking for a way that lets you manually type IP addresses into the four small text boxes like the ones shown.)
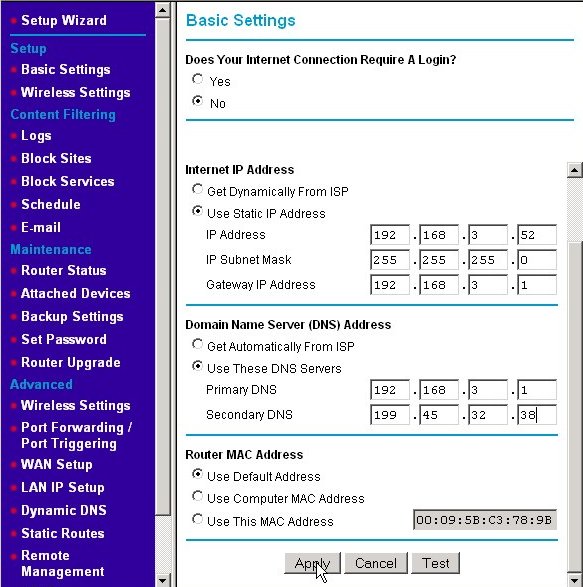
For my example network, I am making believe that my ISP assigned me the static IP address of 192.168.3.52. You would substitute the IP address that your ISP has assigned to you, and enter it into the IP address line. Each part of the IP address goes into a separate text box. (This is just like we did for assigning the internal LAN IP address.) The subnet mask is often set to 255.255.255.0, however, your ISP may give you another value. If so, enter that instead into the IP Subnet Mask line. Your ISP will also tell you what your gateway address is. For my example network, it is 192.168.3.1, which is actually the LAN IP address on my real internal LAN. Substitute yours in those boxes. Finally, enter the DNS server IP addresses given to you by your ISP. (ISPs often don't give these addresses to dynamic IP address customers as the DHCP response from your ISP's DHCP server will include that information. However, status IP address customers need to know that information, so if your ISP failed to give it to your, now's the time to see how good their technical support line is. Press the Apply button to make the new settings active.
Test Your Connection to the Internet
If all has gone well, you should now have connectivity to the Internet. One easy way to test this is to use a web browser to browse to a website that's almost guaranteed to be up. From one of the PCs on your LAN, try one of these websites: https://www.google.com and/or https://www.ebay.com. If you are not able to reach either of those sites, you may need to do a little troubleshooting on your LAN to WAN connection; see Test 5: The Handy-Dandy LAN Ping Test and Test 7: Testing for DNS Functionality. Repeat this test on the other PCs on your LAN (and other devices such as an Xbox [if possible]).
Port Forwarding and Firewall Rules
Port Forwarding and Firewall RulesPort Forwarding and Adding Firewall Rules
This section could also be titled, "How to open yourself up to attack in a civil sort of way." Normally, if your router receives a request from the Internet, your router will not have a matching request from a device on your home LAN. Therefore, it just throws the request (packet) away. This is exactly what you want it to do. Normally those requests are from a hacker trying to see if your computer has no firewall in front of it. If so, they could easily see your published/shared files using a Microsoft file sharing query, for example. In the router's default configuration, no device on the Internet can initiate a request destined for your router or a device on your LAN; devices on the Internet can only send back responses to requests made from the router or devices on your LAN (e.g., browsing a web site).

Sometimes, however, you may want machines on the Internet to be able to initiate a request on a certain port or set of ports that one of the devices on your LAN will serve. The common use of this is when you want to temporarily or permanently provide a server for a game using one of computers on your LAN as the server host. (You should make sure that you have the right to run a server before doing so. See Want to Host an Internet Game Server? Check First.) For example, you might want to run an Unreal Tournament 2004 server so you and some of your friends can have fun chatting to each other over the Internet and killing each other. When an Unreal Tournament 2004 client running on one of friend's computers wants to join your server, it will originate the request with a destination IP address being the public address of your router and also to particular port. (Remember, a port is just a number from 0 - 65,535.) When that request reaches your router, you don't want the router to just drop the packet (for a change). Instead you want to router to forward that packet to the computer running the server.
Most routers will allow you to add a "firewall rule" that will forward traffic, which originates from the Internet and that is destined for a particular port on your router's public IP address, to the same or another port on one of the devices on the LAN. Note that the client sends the request to your public IP address not the private IP address of the server on your LAN. The action of setting up these rules and the router fulfilling them is called "port-forwarding." Some games require multiple ports to be forwarded (e.g., 6800, 1900, 21005). Some require that a range of ports (e.g., ports 27000-27099) be made available.
So the first thing to do is to determine what ports need to be forwarded to your game server. The web site portforward.com contains the procedures for setting up port forwarding for many routers (in addition to the example we're going to have here) and also a list of common ports that need to be forwarded for a number of games and other applications. Unfortunately, I found it missing some detail as the procedures are written in a generic fashion. Some games are also not in the list. When that happens do a search at http://www.google.com and use “<insert game's title here>” firewall ports as the search phrase. (Putting the game's title in double quotes makes Google search for that exact title as a single search term. For example, using "Unreal Tournament 2004" will find only those pages that have those words together and in order - rather than the words unreal, tournament, and 2004 as individual terms. That cuts down a lot of extraneous links from being returned.)
After a little digging in the search results, we find that UT 2004 servers receive requests on UDP ports 7777 and 7778 (Query Port) and 7787 (GameSpy Query Port) from UT 2004 players wishing to join the server. Additionally, the server will send TCP requests using the local port 28902 to the UT 2004 Master Server List (so that your server is put into the list of servers that the UT 2004 players see). However, since that TCP request is an outbound connection initiated by your UT 2004 server, you usually don't need an explicit rule for it.
We'll show setting up the necessary port forwarding by using the same Netgear WGT624 used in our previous examples. Other routers won't have port forwarding in exactly the same place, so you may have to search your menus for it. (This is where the pages at https://portforward.com/ can really help.) As we always do, start your session by logging into the router as shown in section Connecting to Your ISP Using Dynamic IP Addressing. Then, from the Basic Settings screen, choose the Port Forwarding/Port Triggering menu item under the Advanced menu as shown here.
That will bring us to the Port Forwarding/Port Triggering page as shown below.
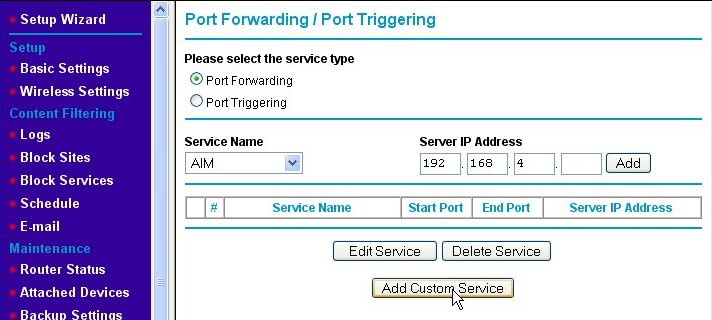
Make sure that the Port Forwarding radio button is enabled (if your router has such a button or check box). Click on the Add Custom Service button, which will take us to the Ports - Custom Services page.
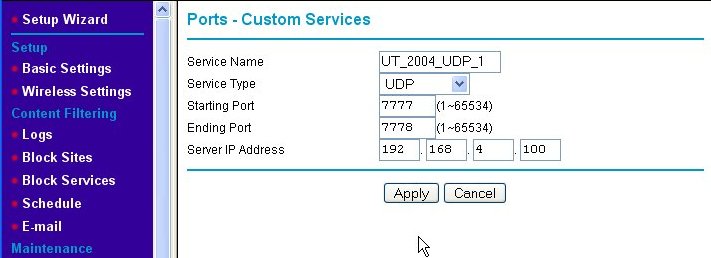
The Ports - Custom Services page is where we add the new port-forwarding rule for our game server. First, we enter a Service Name for our new rule into the text box, which in this example is "UT_2004_UDP-1." Then, we indicate that we wish this rule to apply to request sent using the UDP protocol by choosing UDP from the Service Type pull-down box. Next, since ports 7777 and 7778 are next to each other, we enter them as a range of ports (even though it is a short range) into the Starting Port and Ending Port text boxes, respectively. Finally, we type in the Server IP Address. Note that the IP address used is outside of the range of IP addresses that the router's DHCP server serves. This means that we assigned a static (fixed) IP address to the game server. Since the rules we're setting up are specific to one IP address, we like the game server's IP address to be set to that and never change. DHCP cannot guarantee this, so we use static IP addresses which do. (See Fixed/Static IP (Manual IP) Assignment for information about assigning a fixed IP address to your game server machine.) When we hit the Apply button, we are back at the Port Forwarding/Port Triggering page, but the rule we just added is now shown on the page.
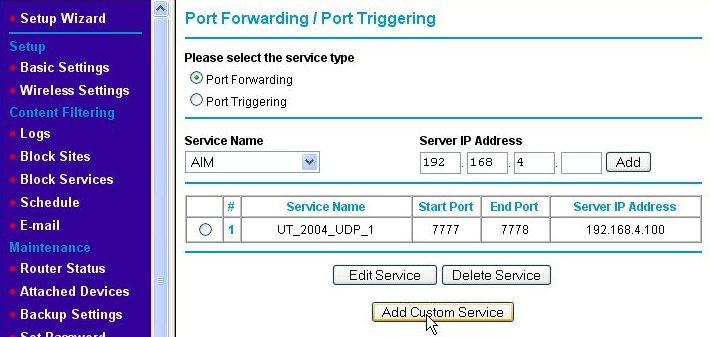
We need to add a second rule for UDP port 7787. We do this by again clicking on the Add Custom Service button and entering the information for the second rule as shown below.
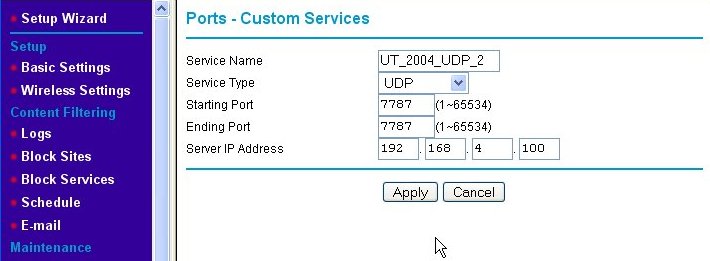
We name the second port-forwarding firewall rule "UT_2004_UDP_2." Note that the starting and ending port numbers are the same when defining a rule for a single port. Again, we press the Apply button and are returned to the Port Forwarding/Port Triggering page, but this time, both of the new rules are shown.
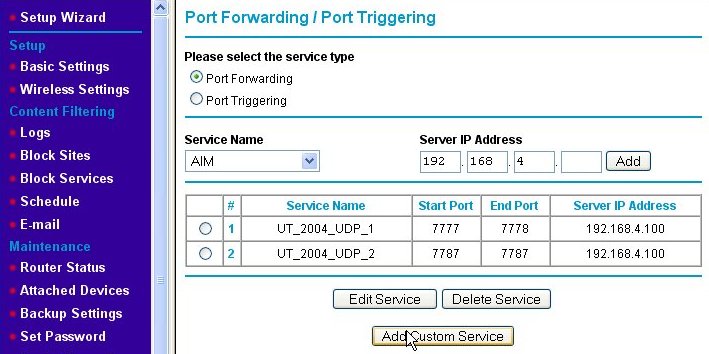
Now, we've added the port-forwarding rules, but there is one extra thing that needs to be done for this particular game server after it is installed. That is to edit the UT2004.ini file (using Notepad or some other plain text editor), search for the lines:
[IpDrv.MasterServerUplink]
DoUplink=True
UplinkToGamespy=True
SendStats=True
ServerBehindNAT=True
DoLANBroadcast=False
and change the ServerBehindNAT from "False" to "True" as shown. This solves a specific problem that makes the server behave itself when behind a NAT firewall such as the Netgear WGT624.
Maintaining Security with Port Forwarding
Maintaining Security with Port ForwardingMaintaining Security with Port Forwarding
Now that you know how to open yourself up to attack in a civil manner, a few words of caution are in order. In ancient Internet times (i.e., 10 years ago or more), there were two approaches to how to set up a firewall. The first approach was to open all ports to all internal machines by default. In this approach rules were created to restrict traffic on those ports known to be "bad" or sources of trouble. This tends to make the life of system administrators easier because most traffic will be routed through the firewall by default. Unfortunately, as time went on and viruses and Trojan horses appeared using more and more ports, this approach became too unsafe.
The second approach is to close most or all ports by default and open only those known to be reasonably safe. This makes the system administrator's job tougher because every new service that their organization wants to offer to users on the Internet or services on the Internet to which the organization's internal users want access will often require rules to be added. However, it is much safer from a security standpoint. Because new viruses that exploit different weaknesses of operating system services found at certain ports and Trojan horses that use different ports than previously known ones, opening ports without a good reason is just a bad idea. All home office/small office routers I have used thus far have adopted the second approach by default, but can be made to operate under the first approach simply by opening large ranges of ports in the rules table.
You might be surprised to learn that your personal computer is most likely a server. No, I didn't say if you have a Windows Server 2003 machine or the like. I'm talking about any right-out-of-the-box, plain-Jane, straight-up PC you can get at Best Buy. Remember that whole topic about connecting up your home PCs so that you can share files, printers, and the like? Guess what? Doing that also makes them servers in every sense of the word. The File Sharing and Printer Sharing services are just that - services. If you share a folder or printer from your machine to other machines on your network a service is started and begins listening on a port on your machine for requests from other machines just like an Internet web server waits for requests for web pages from your browser. If you want to see this for yourself, open a command prompt window and type netstat -rn as the command. You will see something like the following screen.
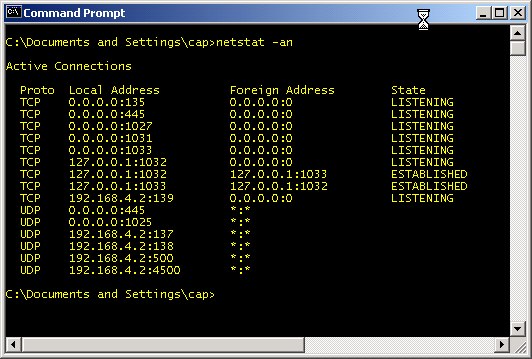
Any of the port numbers given above (i.e., the number after the ":" such as 135 and 445) are services waiting for commands. TCP and UDP ports 135 - 139 and 445 (and according to Microsoft, port 593) are used by the Windows file and print sharing service. TCP Port 1027 is used by Microsoft's Internet Connection Sharing service and the Internet Firewall. UDP Port 1029 is used by Microsoft's Local Security Authority (LSA), which is used to verify and compare user names and passwords (as a part of sharing files and printers). The Sasser worm variants attacked this port and often caused the service to shut down. This in turn would cause the system to reboot itself as a security precaution. Hence, this is a good example of a port you don't want to make available to the Internet. The above list might seem like more services that you would like to have running, but, in reality, that list is about the shortest it ever gets. This particular computer was just rebooted and connected to a router with no access to the Internet when this screenshot was captured. It only gets worse from this point. If you are curious and want to further investigate any of the ports you see in your netstat results, check out the section Test 10: Using the netstat command and TCPView to Check Port Usage.
Your file and printer sharing server will periodically broadcast that it has services available and inquire about other services from other machines. I'm going to assume that you probably didn't intend to share your files or printer with the entire Internet. At one time, I logged unsolicited requests from the Internet that reached my router. I saw Windows machines doing just that many, many, ... many, many times. It was so bad, that I stopped logging all the generous attempts of Windows machines on the Internet to give me access to their files and printers. The amount of this traffic varied from hundreds to thousands per day. I no longer see this traffic at my router, so I believe that ISPs have wizened up and now filter it. That and most people do have router/firewall products in place.
There are certain ports you should never open. Hopefully, it's obvious that the ports mentioned above - TCP & UDP ports 135 - 139, 445, and 593 - should never be open either going to or coming from the Internet. The table below lists ports that should generally not be open to inbound traffic. This means that you should be wary of adding rules to your firewall that allow Internet traffic through to any of the devices on your LAN over the ports listed.
| Port Numbers | Protocol | Use |
|---|---|---|
| 0 - 1023 | TCP/UDP | The ports in this range are known as "privileged ports." They are reserved for usage by specific services like a web server, FTP server, or email server. Unless you have a machine that is running one of these special services, there is no good reason to ever have a rule allowing traffic to any of the LAN machines using any of these ports. |
| 1025-1030 | TCP | Microsoft Remote Procedure Call (RPC) service: This port is used to allow other machines on the network to run services on a local machine. Inside of a LAN this is a useful feature, but Internet machines should not be allowed to run services on LAN machines. These ports also seem to have other uses in Microsoft systems. |
| 1026 - 1027, and to a lesser extent 1028 - 1029 | UDP | In Windows NT, 2000, and XP systems, these ports are used by the messenger service (a.k.a. "net send"). This should not be confused with the Windows Messenger application used for instant messaging (a la AOL Instant Messenger). The intent of the net send service was to allow system administrators to broadcast messages like "Dept. 43 file server going down for 1 hour of maintenance." Unfortunately, spammers started using the service to display messages like "You may have a virus. Visit www.imalowlifespammer.com for details." It's mostly just a nuisance. |
| 1434 | UDP | Probably not a concern to most home network users, but small businesses using Microsoft SQL server will want to keep this port closed to inbound traffic. It's intended to be used to allow remote monitoring of Microsoft SQL Server databases, but it was also the used to exploit SQL Server as one of the fastest spreading worms ever. (If you are a SQL Server user, keep port 1433 closed as well.) |
| 2745 | TCP | Opening this port does not actively open a machine up to attack. It is used by the Bagle and Beagle viruses as a port that allows the virus writer to upload and execute software on an infected machine. If the machine is not infected, there's no harm in opening this port. My personal feeling is, “Why take any unnecessary chances?” |
I derived the above list from looking at the incoming Internet traffic that was logged as denied by my firewall. Then I went to Google and use the port and protocol as a search term (e.g., "UDP port 1434") in order to find out what the ports were (mis)used for. I find http://www.linklogger.com/commonscans.htm a useful source for such information as well.
From time to time, it is a good idea to check the security of your firewall. This is best done from an outside source trying to poke its way in. There are several sites that will scan your IP (i.e., your firewall) for open ports. Most of these do so to try to sell you products for security. One that exists just to try to further security (awareness) on the Internet is (Steve) Gibson Research Corporation's Shields Up!, which is a tool that scans your IP and tells you what you may have open that could be exploited. Click the Proceed button to get to a menu of scan types. I generally like all the first three: File Sharing, Common Ports and All Service Ports. It's good to get in the habit of running this tool regularly. Another good tool is nmap, but that tool is much more complex and probably beyond what most home network users can work with.
The DMZ Machine and Why It Is Evil
A De-Militarized Zone or "DMZ" machine - for the purposes of a home network - is one computer that resides at a static IP address on your LAN that has been designated to be fully exposed to the Internet. Normally, if the firewall receives a packet that does not map to a request made by one of the devices on the LAN, it just drops the packet. However, if a DMZ host has been designated, the firewall will instead route the packet to the DMZ server. That means the DMZ machine is potentially bombarded with requests from the Internet that it may or may not be prepared to handle. Many of those requests will be attempts to hack or infect the DMZ machine.
The security risk to the DMZ machine is high, so why would somebody wish to designate a DMZ machine? A good reason for having a DMZ machine is when you want a machine to be outside of the firewall in order to be a dedicated server (web server, mail server, Unreal Tournament 2004, etc.) and you are willing to isolate that machine from the rest of the machines on the LAN as much as possible. Unfortunately DMZ servers are usually used for a "bad" reason. Sometimes, it is very complicated to set up all the port forwarding firewall rules necessary for a particular game or other server. Some require three, four or more rules to be added. Some routers may not support the number and types of firewall rules that need to be added. Just designating the machine as a DMZ server seems like a good alternative because the work of adding those rules is avoided.
When you designate a computer as a DMZ machine, you've effectively placed it outside of the firewall protection provided by the router. Therefore, if you're going to have a DMZ machine, treat it as a leper. Assume it has been compromised the moment you attach it to the Internet. Don't store any sensitive data on it - up to and including reformatting the machine and reinstalling a fresh copy operating system before starting to use it as such. Only designate a machine as the DMZ machine if you are not going to use it for any other purpose. Install a software firewall with only the only open ports being those needed expressly by to the server and a few other services like outbound ports 80 and 443 (for http and https, respectively).
More importantly, the other machines on your LAN should be protected from the DMZ machine. Install personal firewalls on every other machine and device on the LAN and configure those firewalls to deny any traffic from the DMZ machine with the exception of the ports it's been specifically set up to use for whatever service it is offering. That way, if the DMZ machine does get compromised, the other machines on the LAN may remain safe.