Internet Connection Sharing
Internet Connection Sharing
Even if your all gung ho about getting to the Internet to meet some new, friendly people, talk about their culture, and then wipe them off the face of the earth in StarBlasters 3D Mega-Expansion Pack IV - Online!!!, you still need to do first things first. And the first thing is to have your Local Area Network (LAN) working. If you haven't done that yet, make like a Monopoly player and go straight back to section The Local Area Network, don't pass "Go," and don't waste your $200. If you don't have your LAN functioning among the computers inside your own house and between the computers and the router, then your chances of getting them all sharing an Internet connection are grim.
OK. Now, you've got your LAN a hummin' and all your computers are chatting like Aunt Patty at your last family reunion after she'd had four glasses of wine. Your kids just used the computer upstairs to print 100 pages of "Hi Daddy!" or "Hi Mommy!" or "Hi Parental Unit!" in great big letters in just the last 10 minutes to the printer in your office. Even the cat just sent a fax to PetsRUs for more catnip. That's great! Now, it's time to move on to the next challenge - getting your Internet connection shared to all the devices on your LAN, while keeping everything as safe as possible. With any luck, this will turn out to be pretty anti-climactic because you've already done a good portion of the work.
Permissions and Rights - Are You Allowed to Connect More Than One Computer?

Now, hold on there, hombre! You did read your Acceptable Use Policy as mentioned in the section Want to Host an Internet Game Server? Check First, right? Yeah, I know you skipped that section. It's OK. However, you really should check your ISP's policy on connecting multiple devices if you haven't already. Most ISPs don't care and many even will sell or rent you the equipment (they recommend) to help. A (wireless) router/firewall may even have been included with your ISP's "connection kit" (or whatever they call the hardware and software supplied with your new service). Other ISPs say it's OK to hook up multiple devices if you pay them extra. Some just say, "No. One computer and one computer only." (Luckily, this position seems to be rapidly disappearing.)
Don't hope that you can clandestinely hook up your desktop PC, your laptop and your Xbox 360 and the ISP will never know. Even if you are going through a router, which masks the devices on the other side, your ISP can tell if they choose to check. That said, most ISPs nowadays understand that a house with multiple computers, gaming consoles and other networked devices is just the way things are. They've learned to embrace it. (As in, they've learned they can make money on it by selling you upgraded packages with faster connections and equipment to support multiple computers and other devices like the Xbox 360, iPad and TiVo DVR.) Assuming this is not a stumbling block, let's move on.
Internet 101
In order to understand some of the things that will be done while setting up your broadband sharing network, it's important to have a basic understanding of how the Internet functions. There are a number of really good web sites with tons of information on the subjects introduced in the next few sections. This is intended to be really brief introduction with just enough information to help make sense of the tasks to be done here.
Introduction to the Domain Name Service
We need to digress a moment and talk briefly about how domain names and IP addresses work on the Internet. First, understand that the Internet operates on IP addresses like 121.22.47.219 rather than (domain) names like www.neatwebsite.com. People, however, have a terrible time remembering numbers, so a way was devised to equate a name to an IP address. When you open a web browser and go to the URL http://www.neatwebsite.com/, something interesting happens. Remember those Domain Name Servers (DNSs) that your router gets from your ISP (or that were explicitly given to you by your ISP)? The purpose of a DNS is to translate names like www.neatwebsite.com into an IP address your browser can use.
It's a lot like the process of looking up someone's name in the phone book; you translate a business' or person's name into a telephone number in order to connect to them by telephone. In DNS parlance, this is called "resolving" the name.
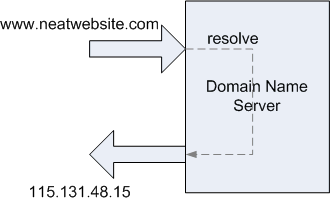
Your browser will consult one of your ISP's DNS servers and ask for the IP address that has been assigned to www.neatwebsite.com. The DNS server will respond with the IP address. Your browser will then make a request for a web page from the web server at that IP address. Every name you type into your browser's address bar must eventually resolve to a single, unique IP address. When the web server sends you back a web page, it sends it to the IP address that was included in the request. Just like the web server at www.neatwebsite.com, your (return) IP address must also be unique. Otherwise, there would be no clear path for the web page to find its way back to you.
Private IP Addresses
So now you might be asking yourself why talking about DNS servers was important when the topic is supposed to be your router. (Go ahead. Ask yourself. We'll wait.) Recall that when we set up our internal network, we used IP addresses starting with 192.168. If you stop and think for a moment, thousands upon thousands of people may have purchased the same router that you did. Many of those people left the internal LAN network at its default settings (e.g., 192.168.0.1). That means that at any given moment there are probably thousands of devices connected to the Internet with their LAN IP address set to 192.168.0.1, 192.168.0.2, etc. Why don't web servers on the Internet get confused when trying to figure out which 192.168.0.2 to return a web page to? The answer is that servers on the public Internet never see or use those addresses.
IP addresses that start with 192.168 are special ones that are called "private" or "non-routable" IP addresses. What this means is that these addresses have been set aside for use by businesses and home users to use internally. You will never find a public web server at the URL http://192.168.0.1 for example. (You could, however, create your own internal "Intranet" web server at that address, and that's fine.) Likewise, the return IP address for the web page you requested would never be 192.168.0.2, for example. It will always be the IP address that your ISP assigned (temporarily or statically) to your router. All Internet data destined for all computers and other devices on your LAN, initially arrive at your router using that public, routable IP address. It's up to the router to figure out which computer or other device attached to your LAN should receive the data (if any).
Introduction to Network Address Translation
How does a request for a web page from one of the machines on your internal LAN to a web server somewhere out on the Internet ever get back to right machine? After all, we purposely assigned one of those private IP addresses to it (either dynamically using DHCP or statically), and those can't be used on the Internet. The answer is that the web server that is out on the Internet never sees that private IP address. Instead, it sees the unique, public, "external" IP address that was given to you by your ISP (again either dynamically or statically). That IP address is guaranteed unique. How this gets done is part of the magic that is your router. The majority of home network routers are "NAT-enabled" routers. That means the router comes out of the box ready to perform what is known as Network Address Translation or "NAT". For this discussion, the simple explanation is that the router will note a request made by a device on the inside LAN that is destined to a device on the Internet (or WAN). This would be something like your web browser requesting a page from 115.138.48.15 to use our http://www.neatwebsite.com/ example above. (Remember, your browser would have already contacted a DNS server to resolve the name www.neatwebsite.com to its unique, public IP address.)
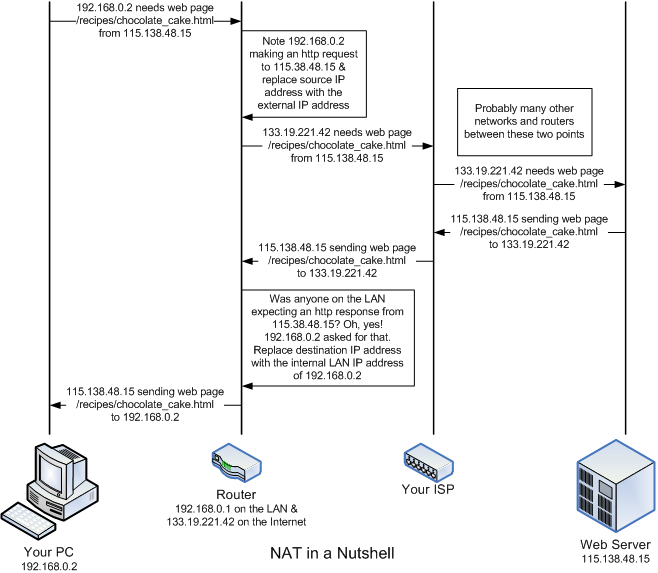
The router will replace the internal, private IP address (e.g., 192.168.0.2) originally found in the request as the source address with the public IP address assigned to your router and send the request on to the web server on the WAN connection. (Let's say it's 133.19.221.42 for this example.) When the web server returns the page you requested, it will send it addressed to the requestor's source IP address (which the router changed to your public IP address). (The source IP address for the request becomes the destination [or target] IP address for the response.) When the web page arrives back at your router, the router will determine which machine on the LAN made the original request for the page. The router then replaces the unique, public IP address given as the destination for the page with the internal, private IP address of the machine that the original request came from. Then is transfers that data onto the LAN-side of the router for the originating device to receive. This is how the router shares your public (WAN) IP address among the devices on your LAN. As far as the world knows, you only have one device on the Internet. Your router knows better. I took about 30 shortcuts in that explanation, so research the topic on the Internet if you want to know more.
I will take a paragraph to note that there are routers that do not use NAT or use NAT only on certain portions of the internal LAN. These routers are most often used by medium to large businesses (and assorted computer geeks that just can't help themselves). This type of network is beyond the scope and goal of what this guide is trying to accomplish. If a router isn't using NAT for a portion of an internal network, then the devices on that portion of the network must be assigned unique, public IP addresses just like the router itself. Larger businesses (like Amazon.com and Google.com just to name a couple) may have dozens of public IP addresses on both internal and external segments of their network. (I don't know the actual network layout of either of those companies, so I'm just making an educated guess.) Most home and small business networks don't have this need. (At least, not yet.)
Using NAT also provides a level of protection for your internal LAN. The enterprise-class routers that make up the major backbone of the Internet will not route private IP addresses in any direction. (Your typical home network router will usually route private IP addresses either way.) Since the IP addresses you are using are private, a hacker from afar cannot pretend to be a machine on your internal LAN by assuming one of your internal addresses. Such traffic would likely be squelched before it could reach you. Additionally, because of NAT function of your router, any packets sent from your Internal LAN appear to be sent by your router. A hacker would have to attack using your external IP address as the target. That's relatively simple to do since hackers tend to attempt to hack a range of addresses they know an ISP allots to clients. They also have to guess you are using NAT. That's also a safe bet. Using your external IP address as the target, a hacker would have to monitor the outgoing traffic from your router and construct a packet with what your router is expecting as a response (to an active request from one of the attached network devices) at a particular moment in time. Since the router's expectations change with every request made from an internal device, a hacker would have to monitor the traffic, find a request worth attacking and then generate and send respond very quickly (before the actual recipient does). This would only work if the attacker is very "near" to your router from a network perspective. In general, this is just not worth the effort. It's far easier to go after targets without firewalls or NAT addressing. Even today, there are ISPs that barring any effort on your part will connect a computer to the Internet with little or no firewall protection. Don't be one of those. If your ISP doesn't supply a firewall router with their service, go buy one of your own.
Introduction to Firewalls and Ports
In addition to the NAT capability, the typical home router will include some sort of "firewall." A firewall is a program built into the router to specifically permit or specifically deny different types of network traffic from passing through. In addition to IP addresses, which we've already discussed, a request for data (an email body, a web page, etc.) is also destined to a particular "port" at that IP address. The port is a delineated by a number from 0 to 65535. Having multiple ports allows a single IP address to be requesting multiple types of services over the Internet (and sending data in response to requests) in parallel. It also allows the same server to service more than one type of request. The ports from 0 - 1023 are called "privileged ports" and are assigned to well-recognized services. For example, when you a request to view a web page to a web server, it will usually be sent as a request to port 80 of the web server's IP address. (If the web page is being sent as a secure page to a URL beginning with https://, the port number will usually be 443.) As mentioned in the previous section, in order to find out the IP address of that web server, you first resolve its name using a DNS server. The DNS requests from your computer would be sent to port 53 on the DNS server. Since most residential customers aren't expected to run any public servers like a mail or web server, the firewall in most home routers will summarily deny any traffic from the Internet with a destination IP for your home that is attempting to use a port in the privileged port range. Ports above 1023 aren't officially assigned to a service, but many have become de facto standards. These are known as "unprivileged ports." Port 5109, for example, is an unprivileged port often used by AOL's Instant Messenger.
Most people think of a firewall only as a means for keeping unwanted or malicious traffic from the Internet out of your home LAN. While that is true, it is equally important that your firewall is keeping unwanted (or malicious) traffic from your LAN off the Internet. For example, Windows PCs periodically query for and advertise network services on ports 137, 138 and possibly 445. (See the trace log below.) If you are connected directly to the Internet without a router or firewall (software), you are probably emitting these requests at a fairly regular interval over the Internet. For the most part, nobody cares and you are just adding to the unwanted/unnecessary traffic on the Internet. Worse, for those that do care - the hackers - you're pretty well lighting a beacon exclaiming "I'm a noob, and I want someone to rape and pillage my machine, please!" Operating a PC on the Internet without a good firewall in place as the equivalent of smearing your naked body with honey and running headlong into a bear den while screaming at the top of your lungs. A NAT router with a firewall will (usually) keep this information from finding its way on to the Internet.
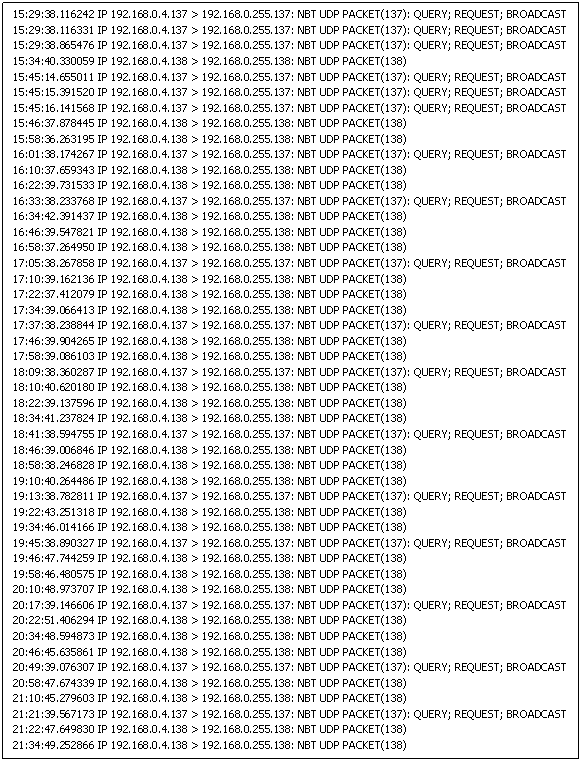
Network Trace of Microsoft Windows Machine Sending Out Periodic Broadcasts
Most ISPs now do a fair bit of screening traffic for you. For example, I log all network traffic that my firewall rejects. I'm paranoid that way. With my previous ISP, I had to stop logging the requests to ports 135-140 and 445 that my router denied. There was just so much of it, it filled my log up. My current ISP must be squelching that traffic somewhere upstream, because I see very little nowadays. A good router with a firewall will keep that traffic inside your LAN thus reducing the amount of useless traffic on the Internet. It also helps to make your home network and router less conspicuous and therefore, less of a target.

Firewall's also protect you to some degree from the effects of a Trojan horse program should you get one. The majority of the Trojan horse programs that I encounter in the wild are being delivered via email rather than an attack on my IP address directly. (The direct approach does not work if you have a reasonable firewall in service, so hackers have switched delivery mechanisms.) If a Trojan should slip through your virus/Trojan detection software (You do have virus/Trojan software on your machine, right?) and install itself, a firewall may still render it inert. If the Trojan's purpose is to wipe out your machine, the firewall won't stop it. However, a lot of Trojan's are designed to find a PC with high-speed connectivity and turn it into some sort of slave server. The Trojan will attempt to contact some sort of controller to let it know it's ready to receive commands. A couple popular use for this type of Trojan is to turn your PC into a host for illegal file sharing or as a sender for email spam. A well-configured firewall may possibly keep that the Trojan from contacting the controller and may keep the Trojan's controller from sending commands to the Trojan running on your local PC.
Most firewalls in home routers are "stateful packet inspection" (SPI) firewalls. With an SPI firewall, the firewall keeps track of all requests made by devices inside your LAN to destinations on the Internet (i.e., connections made to Internet servers). When traffic (a.k.a. a packet) from the Internet reaches your firewall, it should match one of the outstanding requests. If it does match, the firewall passes it to the LAN so it can reach the device that requested it. If it does not match, the firewall drops or rejects the packet. This essentially comes for "free" for router makers if they support NAT (and I can't think of one that does not). Since the router is already tracking connections for the purposes of NAT, SPI is already there.
There is a difference between dropping and rejecting a packet. If a packet is rejected, the router replies to the sender indicating the reason for the rejection. If a packet is dropped, the packet is simply squelched by the router with no indication to the sender what happened. Most home routers drop packets rather than reject them as this is simpler to implement and dropping packets is also stealthier. If your router tells a hacker it's rejected the packets they sent, they know you are there, but that they need to try another approach. If your router simply drops the packet, you don't appear to be there at all and presumably the hacker will go look for a likelier target.
This approach works for home users because most of us operate on an information "pull" model. That is, nothing is sent to a machine on our LAN out of the blue. We use a browser to request a web page and a web server somewhere on the Internet responds. When we get our email from an Internet email server, we make the request for it. Even when we play a game on the Internet, we usually join a centralized server; we proactively start the connection.

The providers of those services - the email servers, game servers, web servers, and so on operate on the model that requests for their services will be initiated from many locations outside of their "LAN." That is, they operate on a "push" model - they will be pressed into service as needed. Therefore, they require a different sort of firewall. That isn't to say your firewall is necessarily incapable of allowing you to host services. The section on Port Forwarding and Adding Firewall Rules goes into this in some detail.
- Printer-friendly version
- Log in to post comments
